Provisioning
Introduction to provisioning
Provisioning is the process of automatically creating, updating, and deleting user accounts and groups in IAM based on information received from an external identity provider. You can also use the information to improve the user experience by setting the user's preferred language, time zone, and user group.
Automatically create or update users
Indicium main administratorIf you want to enable provisioning (see Register OpenID providers, you can set up a template to automatically create or update users in IAM, based on the claim values received from the OpenID provider. Users will be created and updated if they return authenticated from the OpenID provider.
You can configure the template before you enable provisioning.
menu Authorization > OpenID providers > tab User template
A number of fields in the user template are available for mapping.
- Claim values - User fields that you can set to the value of a claim.
- Default values - These will be applied when no value is received for the claim or if the provided claim value cannot be parsed to the right format.
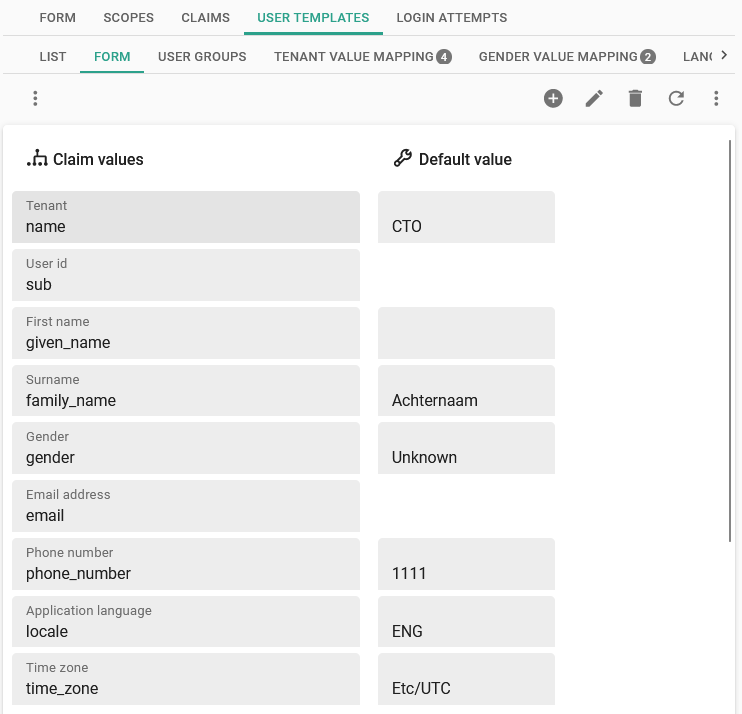 Create a template for creating and updating users
Create a template for creating and updating users
Update scopes and claims
Indicium main administratorScopes and claims can be updated in two ways.
After you have added a new OpenID provider or updated the metadata URL of an existing OpenID provider, you will be prompted to update the available scopes and claims using the metadata endpoint.
You can also reload the scopes and claims manually:
menu Authorization > OpenID providers > all tabs
-
Execute the Reload scopes and claims task
.
-
Select Yes to the following message to visit the URL and update the registered scopes and claims available for the provider.
"Do you want to load the scopes and claims using metadata endpoint
https://login.microsoftonline.com/name/version/.well-known/openid-configuration?"
You can modify scopes and claims if the information cannot be loaded automatically from the metadata document.
Manually modify requested scopes
Indicium main administratormenu Authorization > OpenID providers > tab Scopes
The scopes allow you to request specific information about users. They may also request to allow certain privileges, so be aware not to enable more than needed. Not all scopes are necessary to retrieve the desired claims for user matching or provisioning. We advise you to request as few scopes as possible.
- openid - The openid scope is always requested.
- profile - Deselect if, for example, your Identity Provider does not support the profile scope.
- email - Some Identity Providers (such as Google) will only provide the email claim type if the email scope is requested specifically by the client.
See also Manually update mappable claims.
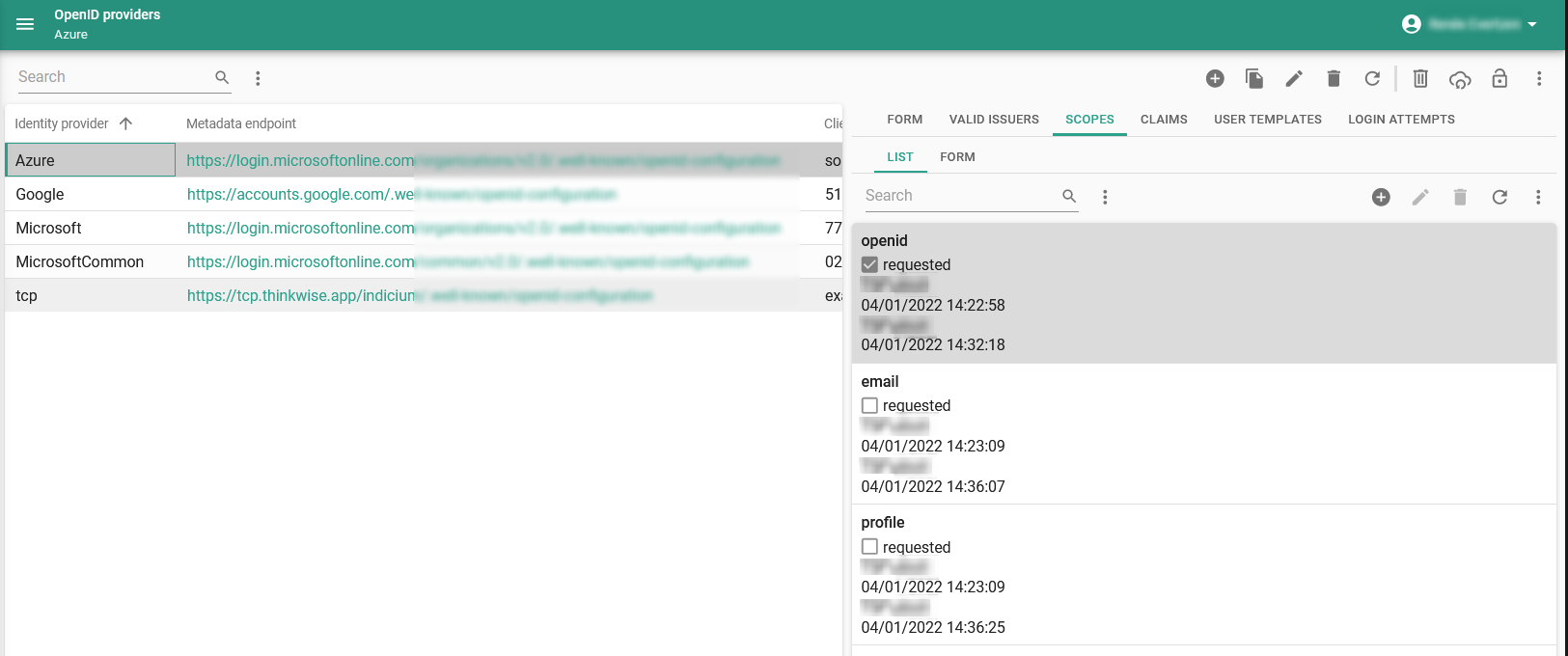 Modify scopes to request user information
Modify scopes to request user information
Manually update mappable claims
Indicium main administratormenu Authorization > OpenID providers > tab Claims
Claims are bits of information about the user that become available when certain scopes are requested. The scopes required to retrieve the available claims are unknown and should be checked with the OpenID provider. For example, some OpenID providers include the email claim in the openid scope. Others require you to request the email scope to which the user may need to consent.
- sub (meaning: subject) - The sub claim has a value that uniquely identifies the user with the OpenID provider. This claim is always available because it is mandatory to include it in the openid scope.
- iss (meaning: issuer) - The iss claim is only available if either all issuers or additional issuers are allowed. This claim contains the issuer's URL.
The information you specify here, can also be used for mapping the values of a claim to known values in IAM.
See also:
- The sub claim is unique for each application in the Azure AD tenant. For example, in a DTAP environment, a user would get a different sub in Production and Acceptance. Instead, you could use oid (meaning: object id), which is a unique identifier for the user across applications in the Azure AD tenant. The profile scope is required to receive this claim. For an overview of all available claims, see the Microsoft documentation about ID token claims reference.
- A cloud-based Azure AD Group that is not inherited from a local AD group only provides the Group ID, not a sAMAccountName.
- In Azure AD, you can add the groups claim in menu App registration > Token configuration > Add groups claim.
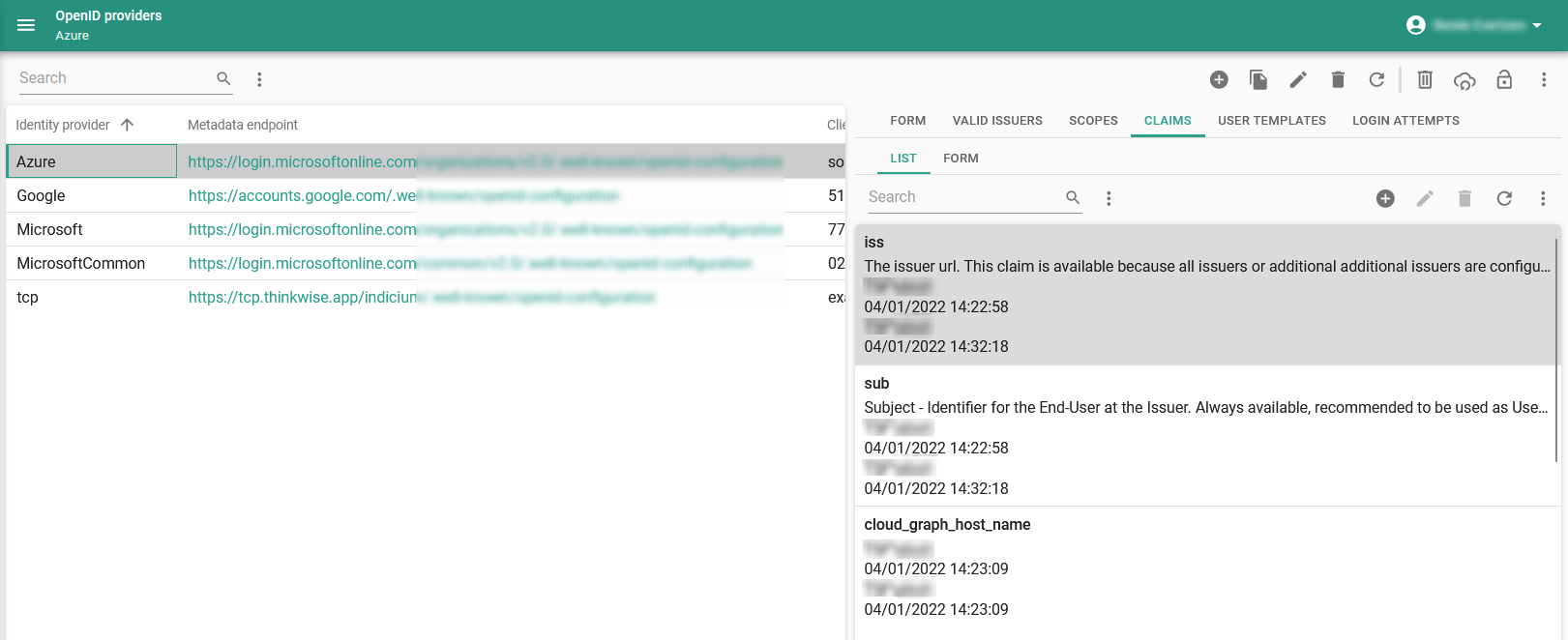 Modify claims to specify the information you expect to retrieve, so it can be used for mapping
Modify claims to specify the information you expect to retrieve, so it can be used for mapping
Add and map claims for Azure AD user provisioning
Indicium main administratorWhen setting up Azure AD User Provisioning, you need to add and map the following claims in IAM manually:
- given_name, mapping to First name in the IAM User Template.
- family_name, mapping to Surname in the IAM User Template.
- groups, mapping to User Group in the IAM User Group Template.
After adding claims, Indicium needs to be restarted.
Value mapping for categorical user fields
Indicium main administratorIt is not always possible to directly use a Claim value as a Tenant, User id, Gender, Application language, or Time zone. These are categorical values in IAM, often not known by the OpenID provider and unlikely to be included in the same format in the claims. For example, you may want to map the iss (issuer URL) claim value to a tenant in IAM or a locale or country claim value to an application language in IAM.
To allow this, you can provide a value mapping for a number of categorical user fields:
menu Authorization > OpenID providers > tab User template
- Tenant - tab Tenant value mapping.
- Gender - tab Gender value mapping.
- Application language - tab Language value mapping.
- Time zone - tab Time zone.
In these tabs, you can map the values of the chosen claim to known values in IAM. A value mapping for these user fields will become available when the claim to be used has been set.
If the Claim value does not match any mapping, the Default value configured in the user template will be used. So, if a mapping is available, the claim value will not be used. In reverse, if a claim has been configured but no mapping specified, the Claim value will be used.
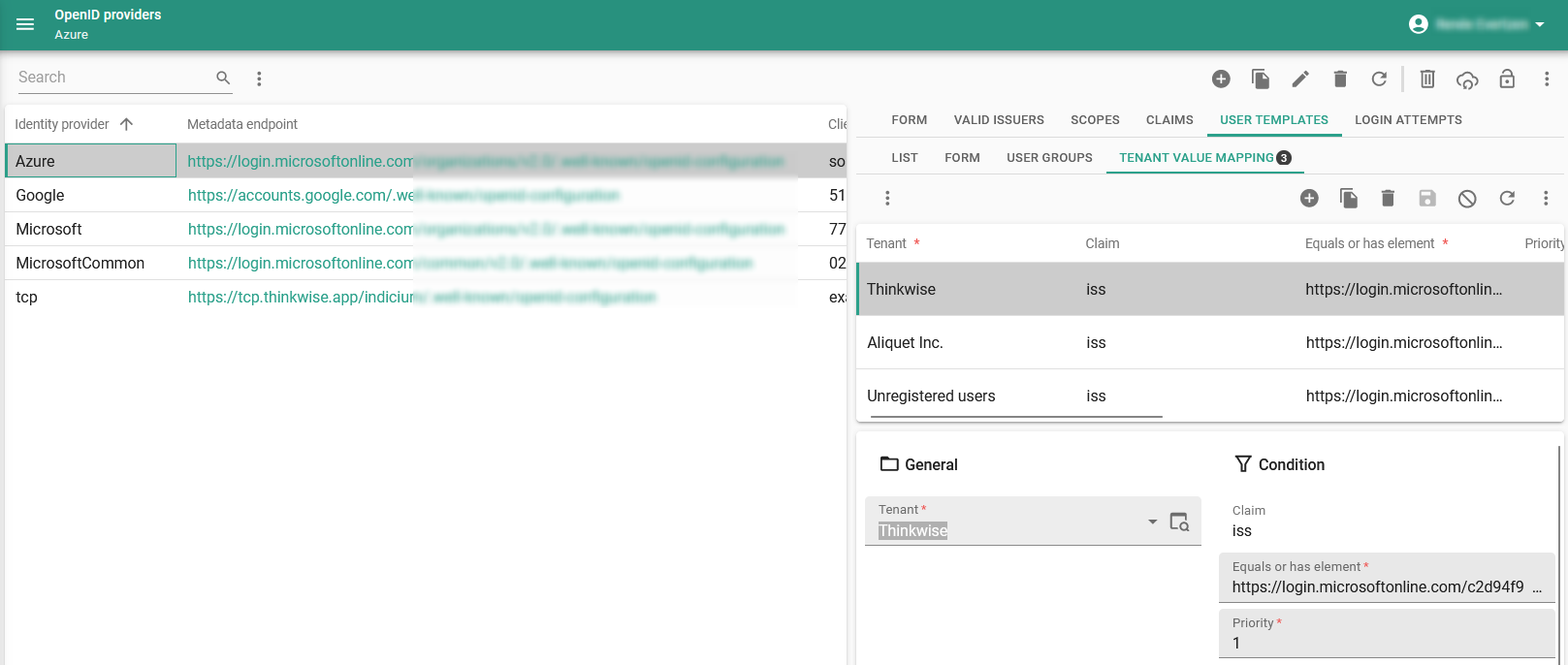 Tenant value mapping in a user template
Tenant value mapping in a user template
For a value to be applied, the claim will have to equal the provided value or, if the claim is a JSON array, will have to contain an element that equals the value. So, multiple matches are possible, but only one value will be picked for the user to provision. In that case, the priority (ascending) will be used to pick a value.
Using the example below, if the locale claim contains the value {"en-GB", "de", "fr" }, the application language DE will be selected, as it is the first
matched value with a higher priority than ENG.
The Application language and Time zone will only be set once and not be updated to prevent the provisioning mechanism from overriding user preferences.
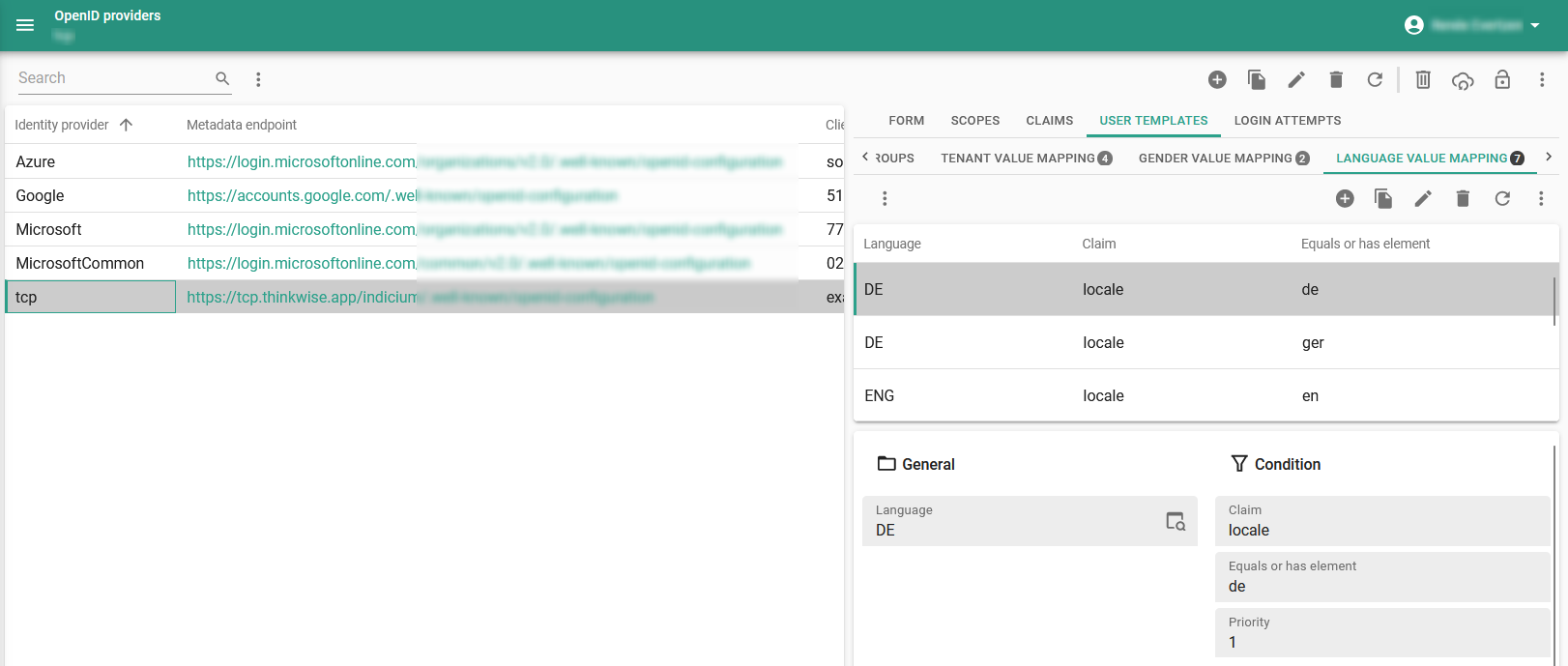 Example: Language value mapping
Example: Language value mapping
User groups for provisioning
Indicium main administratorIf you configure user groups, they can be automatically created or updated for the user.
You can specify a user group multiple times. If a user group is mapped via multiple conditions, only one of them needs to be satisfied.
menu Authorization > OpenID providers > tab User template > tab User groups
- User groups without a Condition will always be provided to the user.
- If a Condition is active, the claim will have to equal the provided value or, if the claim is a JSON array, contain an element that equals the value.
- A granted user group belonging to a tenant that does not match the assigned tenant for the user will be ignored.
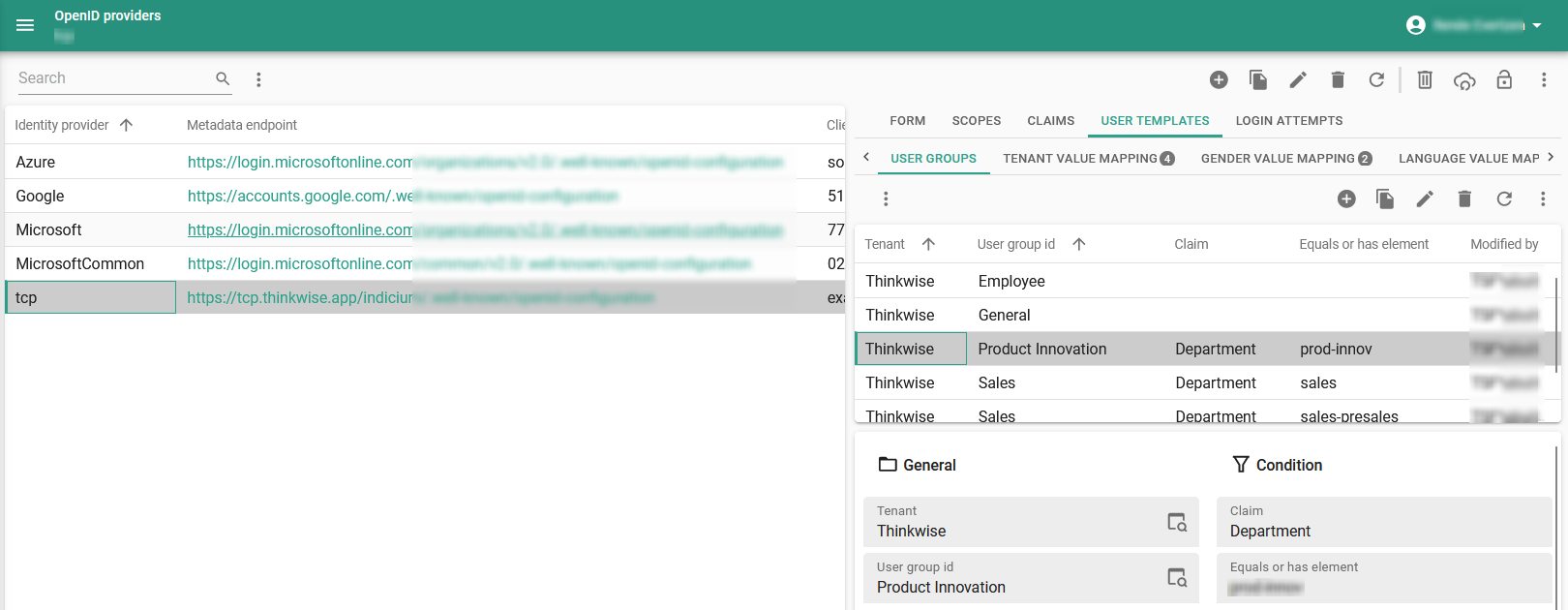 Configure user groups
Configure user groups