Acceptance and production environment reference architecture
Introduction to the acceptance and production environment reference architecture
For the infrastructure of the Acceptance (UAT) and Production environments it’s best when they are identical in architecture, components, configuration, and capacity. Ensuring parity between these environments guarantees realistic user acceptance testing, accurately reflects actual usage scenarios, and minimizes deployment risks. Any deviations could lead to discrepancies in test results, reduced reliability, and unforeseen performance or stability issues in production.
Maintaining infrastructure consistency is essential for reliable deployments, effective troubleshooting, and high-quality software delivery.
Acceptance environment
Purpose
- User Acceptance Testing (UAT), stakeholder validation, and final approval.
User Types
- Product Owners & Stakeholders - Verify features against requirements
- Business Analysts/Test Coordinators - Organize and oversee user testing
- Representative End-users - Limited group for acceptance validation
Access Method
- Typically via secure authentication, including:
- OpenID / OAuth for realistic validation of external authentication
- Internal/managed accounts for users without external IDs
Data
- Realistic, but anonymized or sanitized datasets
Typical Activities
- User scenario testing
- Stakeholder demos
- Sign-off on acceptance criteria
Production environment
Purpose
- Live environment providing stable and secure service to actual users.
User Types
- End-Users/Customers - Full access, performing real tasks and transactions
- Administrators/Support Staff - Monitoring, supporting, and managing the environment
- Operations Team (DevOps/SRE) - Manage infrastructure, deployments, and monitoring
Access Method
- Robust authentication methods required, including:
- OpenID / OAuth for secure external authentication
- Multi-Factor Authentication (MFA) for administrative or sensitive access
Data
- Real, live customer data
Typical Activities
- Real usage, live transactions
- Support, troubleshooting real-time incidents
- Monitoring and proactive maintenance
Environment requirements
The acceptance and production environments must be stable, secure, and representative of the final application deployment. These environments are intended for validation, user acceptance testing (UAT), and live operations. The following technical and functional requirements apply:
- Controlled Configuration - Clearly defined access controls, performance parameters, and security policies. Unlike development and test environments, changes should be strictly managed through formal change procedures.
- AI Configuration - Requires an active (paid) API key to access AI services such as OpenAI or other platforms. API credentials must be securely stored and managed in accordance with internal security guidelines.
- Microsoft SQL Server:
- Version: Standard or Enterprise
- Features: Full Text Search must be enabled
- Production databases must be regularly backed up and monitored for performance and availability
- Security (SSL/TLS):
- Full support for SSL is required to ensure secure client-server communication
- Use of HTTP is not permitted
- Only trusted certificates are allowed:
- Standard SSL certificate
- Wildcard certificate
- Self-signed certificates are not permitted
- Availability & Monitoring - Environments must be monitored for uptime, performance, and security incidents. Logging and alerting mechanisms must support operational oversight and auditing.
- Indicium Service Account - Must have:
- Write permissions on the Indicium directory
- Access rights to both the IAM database and the application database
- Secure management in line with the organization's IAM policies
Cloud
Architecture and connections
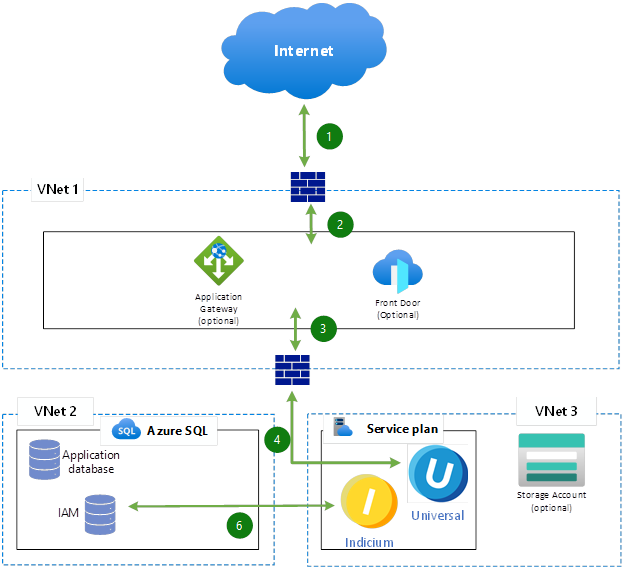 Cloud acceptance and production environment reference architecture
Cloud acceptance and production environment reference architecture
Connections:
- Internet → External Firewall
Traffic originating from the Internet passes through the external firewall. - External Firewall → Azure Application Gateway or Azure Front Door (VNet 1)
Incoming traffic is routed to Azure Application Gateway or Azure Front Door services. - Application Gateway/Front Door → Internal Firewall
Traffic passes through an internal firewall to reach internal VNets. - Internal Firewall → App Service Plan (VNet 2)
Secured traffic is routed to Azure App Service or similar hosting environments. - Service Plan (App) → Azure Storage Account (VNet 3, optional)
Applications may access Azure Storage for files, blobs, or data. - Service Plan (App) → Azure SQL (VNet 2)
Applications communicate with Azure SQL databases for storage, retrieval, and IAM.
Common Ports Overview:
| Service | Typical Port Numbers |
|---|---|
| HTTP | TCP 80 |
| HTTPS | TCP 443 |
| Azure SQL Database | TCP 1433 (TLS secured) |
| Azure Storage | TCP 443 |
Sizing (hardware cloud)
Recommended Specs Cloud:
| Component | Azure | AWS | |
|---|---|---|---|
| SQL | AzureDB | AWS RDS db.m5.xlarge (4 vCPU, 16 GB) | SQL Server (4 vCPU, 16 GB) |
| Indicium & Universal | AppService Premium v3 P2V3 | Elastic Beanstalk m6i.xlarge (4 vCPU, 16 GB) | Cloud Run (Memory: 2 GB) Storage Bucket Class data: Default Class Standard |
Cloud environment setup
For more information about setting up a cloud environment, see:
On Premise
Architecture and connections
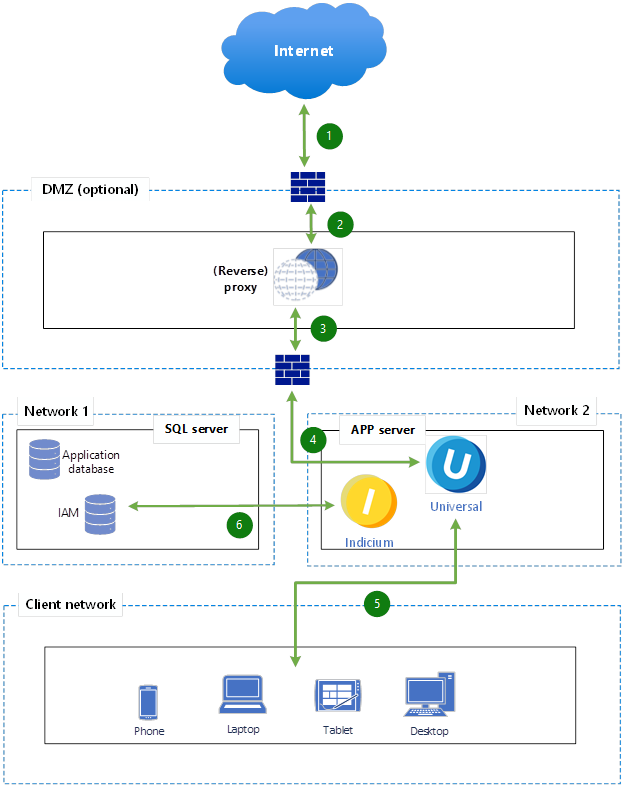 On-premise acceptance and production environment reference architecture
On-premise acceptance and production environment reference architecture
Connections:
- Internet → External Firewall
External user traffic reaches the first firewall, which controls incoming web traffic. - External Firewall → Reverse Proxy in DMZ
Allowed traffic moves to the reverse proxy server located in the DMZ, which acts as a secure intermediary. - Reverse Proxy (DMZ) → Internal Firewall
Traffic verified by the reverse proxy moves through the internal firewall into the secure internal networks. - Internal Firewall → App Server (Network 2)
Application requests forwarded by the reverse proxy reach the internal application servers. - Client Network → App Server (Internal)
Internal clients (phones, laptops, tablets, desktops) connect directly to the application servers. - App Server → SQL Server (Network 1)
Application servers communicate with SQL servers for data queries, storage, and authentication.
Common Ports Overview:
| Service | Typical Port Numbers |
|---|---|
| HTTP | TCP 80 |
| HTTPS | TCP 443 |
| SQL Server | TCP 1433 |
Sizing (hardware on premise)
Recommended hardware specifications (IIS Server):
| Component | Configuration |
|---|---|
| CPU | 4 vCPUs |
| Memory | 16 GB RAM |
| Storage | 100–200 GB |
| OS | Windows Server 2019/2022 |
Recommended hardware specifications (SQL Server):
| Component | Configuration |
|---|---|
| CPU | 4 vCPUs |
| Memory | 16 GB RAM |
| Storage | Windows/SQL installation: 200 GB SQL Data: 200 GB SQL Log: 100 GB Best practice: Separate the installation, data and log locations. |
| OS | Windows Server 2019/2022 |
| SQL | SQL Server 2019/2022 Standard or Enterprise |
On-premise environment setup
For more information about setting up an on-premise environment, see: