Container registry authentication
Introduction to container registry authentication
It is mandatory to authenticate to the registry before you can pull container images. This can be achieved by requesting a token at TCP > Software > Thinkwise containers.
A token contains a username and password, which gives you access to the container images in the Thinkwise Container Registry.
Authentication tokens
Request a token
TCP > Software > Thinkwise containers
-
Execute the Request token
task and enter a Description.
- The description and name of a generated token are visible to the employees of your company, so colleagues can revoke your token if needed. Keep this in mind when you give the token a description. It is possible to edit the description of a token later.
- Do not use the same credentials at multiple places. Generate new credentials with a clear description for each machine or cloud instance you want to use.
-
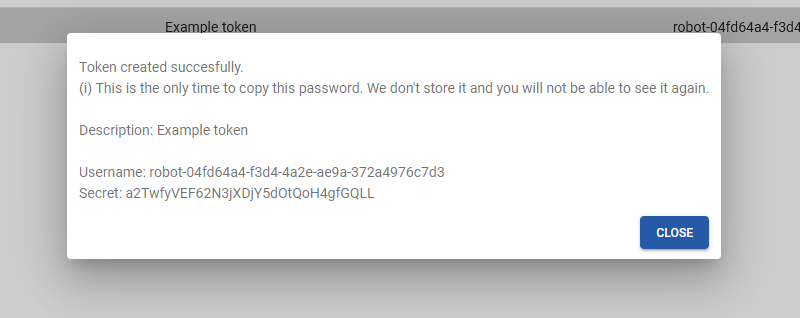
Select Execute to generate the token.
The token contains:
- Username - Username to log in to the registry.
- Secret - The secret/password belonging to this created token.
The secret is shown only once. Apply it directly to the machine you want to the token for.
Edit token description
If required, a token description can be modified. This could be useful when the initial description did not fully match the intended use of this token.
TCP > Software > Thinkwise containers
- Execute the Edit token description
.
Revoke a token
When you no longer require the token, or if it is compromised, you can revoke it.
TCP > Software > Thinkwise containers
- Execute the Revoke token
task.
- Select Yes if you wish to continue.
The token will be deleted. Any machines using the credentials of this token will no longer be able to authenticate with the registry (and thus not be able to pull/update container images).
Log in to the registry
- Docker
- Docker Swarm
- Kubernetes
Log in to the registry:
docker login registry.thinkwisesoftware.com
After executing the command, the shell will prompt for the username and password. Paste the username and secret from the token in here.
For example:
$ docker login registry.thinkwisesoftware.com
Username: <token-username>
Password:
Login Succeeded
Log in to the registry:
docker login registry.thinkwisesoftware.com
After executing the command, the shell will prompt for the username and password. Paste the username and secret from the token in here.
For example:
$ docker login registry.thinkwisesoftware.com
Username: <token-username>
Password:
Login Succeeded
Create a service:
By providing the parameter --with-registry-auth, the registry authentication details will be sent to the Docker Swarm agents.
docker service create \
--name <name> \
--with-registry-auth
registry.thinkwisesoftware.com/public/<image>
For more information about the commands for a service in Docker Swarm, see: https://docs.docker.com/engine/reference/commandline/service_create/
Create a Docker Registry secret:
Be cautious when creating a secret. Each shell will log and save each command to its history file. There are ways to mitigate this, for example by reading the input of the keyboard and storing this as a variable. But this is out of scope of this manual.
The following command will create a Docker Registry secret with the name thinkwise-registry:
kubectl create secret docker-registry thinkwise-registry \
--docker-server registry.thinkwisesoftware.com \
--docker-username "<token-username>" \
--docker-password "<token-secret/password>"
Specify the created Docker Registry secret:
By adding the object imagePullSecrets to the manifest of the pod/deployment, you can specify which secret to use for pulling container images from the specified registry.
...
containers:
- name: <container-name>
image: registry.thinkwisesoftware.com/public/<image>
imagePullSecrets:
- name: thinkwise-registry
...
For more information about Docker Registry secrets in Kubernetes, see: https://kubernetes.io/docs/tasks/configure-pod-container/pull-image-private-registry/