Encryption in Azure
Introduction to encryption
In some cases, Indicium needs access to a secure location for storing encryption keys:
- When encrypting key values such as passwords, client secrets or API keys.
- When using the Encrypt and Decrypt process actions.
- When scaling to multiple Indicium instances.
It is very important to back up these keys. If you lose these keys, the encrypted data in the database can no longer be used and cannot be recovered in any way.
Without this setup, calling the Encrypt and Decrypt process actions in your application will result in an error.
This manual describes how to centralize the storage of this certificate in Azure.
Create a Key Vault for encryption
When using Indicium on Azure, the encryption keys must be stored in a Key Vault:
-
Create a Key Vault on the Azure Portal.
-
Add an "Access Policy" to it to allow the Indicium instance Web App access.
-
Select the Identity menu in the Indicium Web App.
-
Check whether the Identity setting System Assigned is enabled.
-
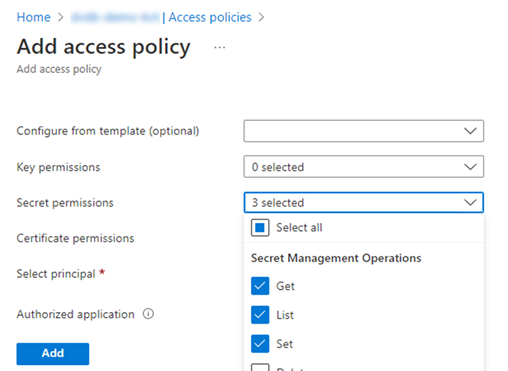
In the Key Vault, select +Add Access Policy from the Access Policy menu on the left-hand side.
-
In the Secret permissions field, select the "Get", "List", and "Set" permissions.
-
In the Select principal field, select your Indicium Web App.
-
Click Add. You are automatically returned to the Access Policy screen.
-
Click Save to save the new access policy.
 Add access policy
Add access policy
Add encryption settings to Indicium
To use the newly created Key Vault, you must set the KeyVaultSecretUrl setting in the Indicium Web App.
In the appsettings.json configuration file, this KeyVaultSecretUrl setting can be configured directly:
"DataProtectionSettings": {
"AzureKeyVault": {
"KeyVaultSecretUrl": "<key vault secret url>"
}
}
Alternatively, you can store this setting in the App Service:
-
In the App Service, select Settings > Configuration from the menu.
-
Add the following Application settings:
Name: DataProtectionSettings:AzureKeyVault:KeyVaultSecretUrl
Value: https://<name-of-the-key-vault>.vault.azure.net/secrets/<secret-name>
When the Key Vault url is configured, Indicium will automatically create a key. Every 90 days, Indicium creates a new version within this key.
Do not delete old versions! When deleting old versions, Indicium cannot decrypt the old data.